After Bleckmann-Dreher's attempts to contact the project were published on Web3 Is Going Great on February 26, Ocean Protocol's founder Bruce Pon commented to say they were "on it", and that he had alerted Data Whale about what appeared to be an issue in the ALGA project. Several hours later, Data Whale announced they would be taking the app offline due to concerns that there was a vulnerability, and that they had contacted the researchers. ALGA was later brought back online after they confirmed the vulnerability was not an issue with their project, but rather with Ocean Protocol itself. Pon acknowledged on February 27 that "there was a configuration issue on Ocean compute-to-data which is being fixed now", and later that day Ocean Protocol cut a new release of their operator engine which appeared to be a patch.
Security researchers desperately try to contact Ocean Protocol about a critical security problem
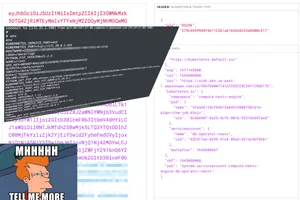
Ocean Protocol is a web3 project promising to help people "publish, discover, and consume data in a secure, privacy-preserving fashion". Recently, they've been promoting the ALGA defi wallet, a project created by an external development team called Data Whale. Security researcher Christopher Bleckmann-Dreher, also known as "schniggie", resorted to publicly replying to one of Ocean Protocol's promo tweets to try to get the group's attention on a security vulnerability he and his collaborator Daniel Matesic ("mtd_0x00") had discovered. The duo found Kubernetes infrastructure that appeared to be completely compromised, and were able to get a shell, call their underlying AWS metaservice, and more. When Bleckmann-Dreher tried to report the bug through Ocean Protocol's Github bug bounty program, he found it was retired. He also tried to contact the team via their security email address, Telegram, and Discord, but received no reply.